Shouting From The Rooftops | Public Key Cryptography
Whenever my friends are splitting the bill for a vacation I prefer having my cash transferred to me online. In 2016, most of us are comfortable doing online transactions, at least, with people we know. There are still a few holdouts though.
Recently after returning from Goa, a friend insisted on giving my share in cash. I couldn’t keep that much cash at home, so I had to deposit it in my bank. I hate having to go to the bank. When I asked him, he told me he never uses electronic payment mechanism. He doesn’t trust the system. He was certain that the moment he logged in there would be an army of spammers, phishers and con artists out to get him.
He’s right about that. The system might not be trustworthy either. What you can trust though is mathematics. Specifically the mathematics behind public key cryptography. I couldn’t understand why someone would inconvenience themselves to avoid a simple transfer. That’s when he told me that he actively avoided online banking or e-commerce of any sort.
Public key cryptography is what enables me to share my credit card details with my bank without sharing them with the millions of people or robots trying to listen in. A basic understanding of public key cryptography can clear up many misunderstandings about online security. At the very least, you can begin to understand the real nature of security flaws on the Internet. I will try to explain the basics of public key cryptography and hopefully save myself a few trips to the bank in the process :)
First off, there are two kinds of cryptography: symmetric and asymmetric.
Imagine you have a secret you’ve hidden inside a box (Maybe its the Answer to the Ultimate Question of Life). Now if just anyone could open that box, that wouldn’t be much of a secret would it? But you are clever. You hire a locksmith to put a lock on the door. He leaves the key with you.
Voila! That is symmetric cryptography!
Symmetric cryptography is great if you have a secret that you never want to share with anyone. As long as you don’t lose the key, your secret will remain safe. (Your locksmith is awesome and knows how to make an unbreakable lock)
But it’s not of much use if you need to share your secret with someone……say your friend who lives on the other side of town. If you sent the box to him, you would have to send the key too. Which anybody could use to open the box.
You take your dilemma to your super-genius locksmith. He scratches his head for a while and fits your box with a new lock.
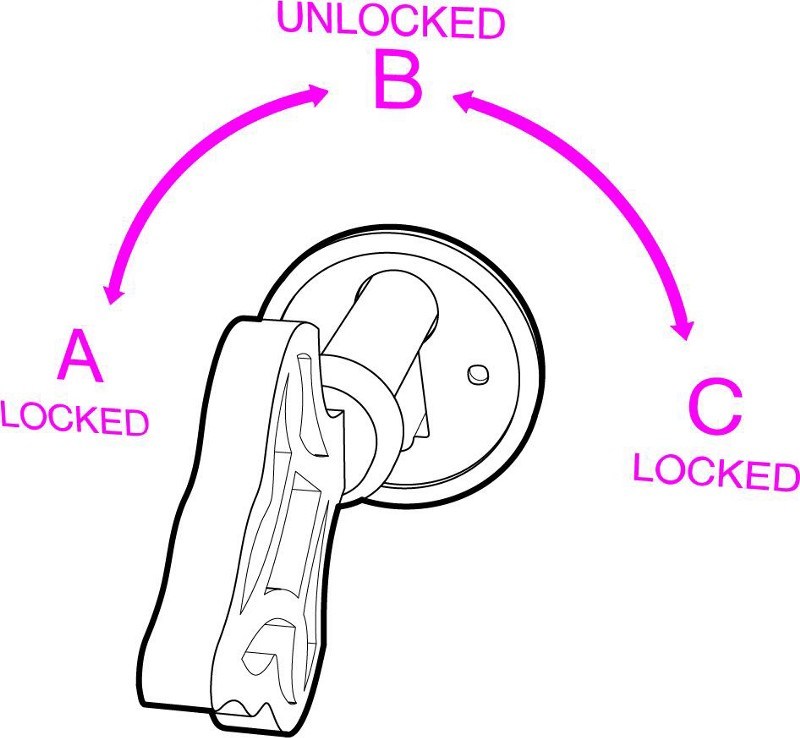
This is a very very special lock. It has two keys!
- Key 1 - Turns only clockwise (from A to B to C)
- Key 2 - Turns only anti-clockwise (from C to B to A)
With this special lock, you can do some amazing things!
You take Key 1 and make it your private key (you don’t share it with anyone. Not even your mom).
Key 2 you make your public key….and I mean public. You make copies and share them with anyone who asks for it (and a few people who didn’t).
You lock the box by turning from B (unlocked) to C (locked) using your private key. You then send me the box with a note saying who it’s from.
A strange box arrives on my doorstep…do I open it? Of course, not….I’m not an idiot! It could be from anybody!
I think about it and realize that it isn’t difficult to know who it’s from.
I take the public key which you had shared with me and try to unlock the box. I move the lock from C to B and I can open. But its not just that I can open it…..I can open it and I know for sure that the box really is from you.
Think about it….if I unlock it from C to B, that means someone locked it by turning from B to C. But only one person in the world can do that…..the one who has your private key…..that is…..you.
If you encrypt (“lock”) something with your private key, anyone can decrypt it (“unlock”), but this serves as a proof you encrypted it: it’s “digitally signed” by you.
Now I have a secret of my own I want to share with you. Of course, I don’t want all the Peeping Tom’s to know! So I lock it by using your public key by turning from B to A.
Now I can send it to you confidently knowing that your private key is the only one in the world which can open this box.
If anyone, even you, encrypts (“lock”) something with your public key, only you can decrypt it (“unlock”) with your secret, private key.
If you were really paying attention you know that when you shared your box with me, it was not really a secure transaction…..anyone with your public key could have opened the lock.
That is why in most real-world transactions there is not just one set of key pairs but two. One is yours, the other is mine. If you wanted to send the box securely to me, you would lock it with my public key knowing that only I would be able to open it……using my private key
Of course in the real world, we don’t really use physical keys to share information. We use something much much more secure…..very very large sets of randomized numbers and characters.
Public-key cryptography enables millions of people every day to securely share their data over the Internet. It’s a godsend without which the modern Internet wouldn’t have grown to the all-encompassing behemoth it is today.